BTLO Memory Analysis - Ransomware (Writeups)
Home Blog CTF Write up BTLO Memory Analysis - Ransomware (Writeups)
BTLO Memory Analysis - Ransomware (Writeups)
Memory Analysis - Ransomware
In forensics category, as we already know that if the title is memory analysis, we need to use volatility tool.
volatilityfoundation/volatility: An advanced memory forensics framework (github.com)
For this challenge, I used python and volatility tool (vol.py) on Kali Linux VM for this challenge.

Q1. Run “vol.py -f infected.vmem --profile=Win7SP1x86 psscan” that will list all processes. What is the name of the suspicious process?
For Q1, we don't have to think about which command to use for check the image profile and suspicious process that is already given in question "vol.py -f infected.vmem --profile=Win7SP1x86 psscan".
So, we just need to run.
# python volatility/vol.py -f --profile=Win7SP1x86 psscan
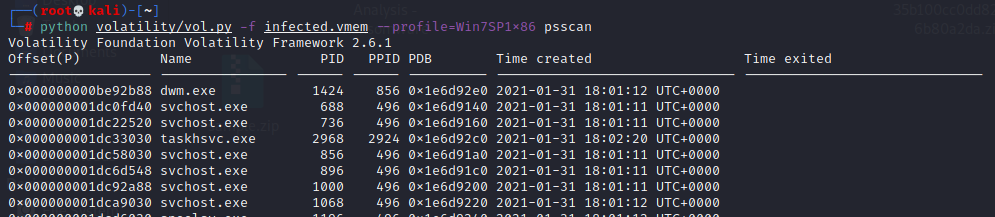
Scroll down to bottom...... you will see an abnormal process with unusual parent ID as shown in below screenshot.
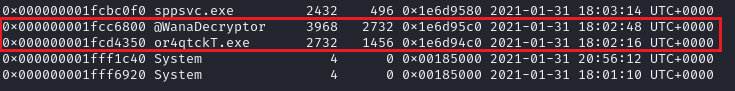
So, answer is @WannaDecryptor.
Q2. What is the parent process ID for the suspicious process?
The parent process ID of @WannaDecryptor is 2732.
Q3. What is the initial malicious executable that created this process?
It is easy to know that the parent process ID (2732) of @WannaDecryptor is the process ID of or4qtckT.exe (executable).
Q4. If you drill down on the suspicious PID (vol.py -f infected.vmem --profile=Win7SP1x86 psscan | grep (PIDhere)), find the process used to delete files.
we need to scan the suspicious PID (2732) with given command.
# python volatility/vol.py -f --profile=Win7SP1x86 psscan | grep 2732
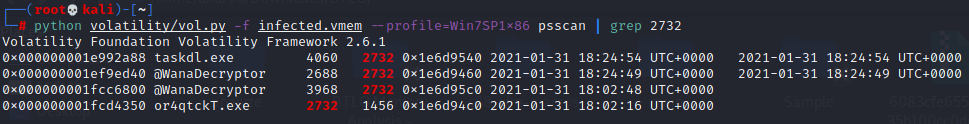
After you run the command, it will show four processes and taskdl.exe is deletion tool for deleting the files.
So, answer is taskdl.exe.
Q5. Find the path where the malicious file was first executed?
For this question, we can use two commands 'cmdline' or 'filescan'.
# python volatility/vol.py -f --profile=Win7SP1x86 cmdline | grep or4qtckT
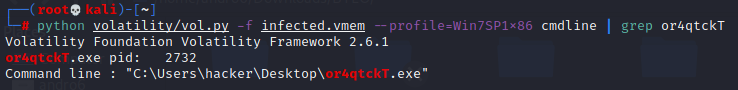
So, answer is C:\Users\hacker\Desktop\or4qtckT.exe.
or
# python volatility/vol.py -f --profile=Win7SP1x86 filescan | grep or4qtckT
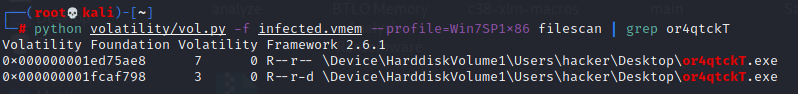
we already know that \Device\HarddiskVolume1 is C: directory.
So, answer is C:\Users\hacker\Desktop\or4qtckT.exe.
Q6. Can you identify what ransomware it is? (Do your research!)
I used two keywords (or4qtckT.exe and @WannaDecryptor) for googling.
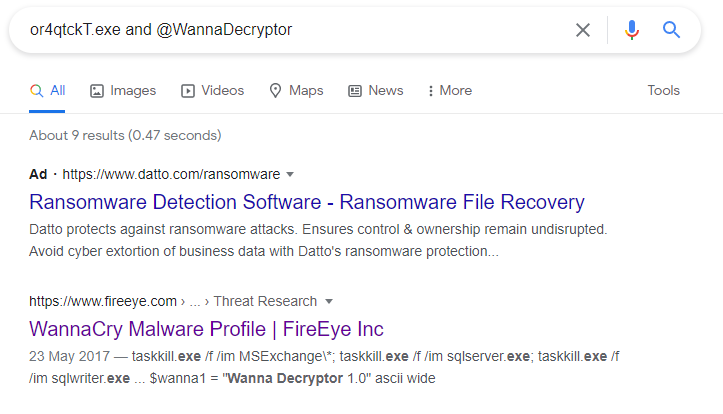
We will see that is WannaCry.
Q7. What is the filename for the file with the ransomware public key that was used to encrypt the private key? (.eky extension)
As I mentioned earlier, let's use that filescan command again.
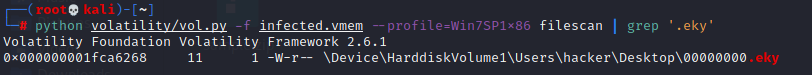
So, the answer is 00000000.eky.
Boom!!!!
BTLO account is https://blueteamlabs.online/home/user/55a47184c78182b03ecfc7